What is OWASP Top 10, and why is it important to application security?
Application security is simply one of the most essential steps in planning for application development. Besides, the level of reliability will determine its success, which will be reflected in the number of active users in the software, for example. And there is no way to talk about security without mentioning OWASP. The collaboration of IT professionals is vital to combat security breaches, shielding systems against leaks of confidential information from companies and users, and unauthorised intrusions. This makes it crucial to monitor and actively participate in OWASP.
Do you want to understand OWASP better and see why it is so important to your company- keep reading.
Table of contents:
- What is OWASP?
- How does the Open Web Application Security Project OWASPwork?
- Why OWASP is important?
- What is the OWASP Top 10?
- How are the top 10 vulnerabilities used, and Why is OWASP Top 10 such a big deal?
- Top 10 web application security risks
- Which security vulnerabilities are new/ have been removed from the list?
- How to keep your web applications secure in the future
- How can Synopsys help?
What is OWASP?

OWASP is an acronym for Open Web Application Security Project. It is a nonprofit organization committed to improving software security. OWASP operates under an open community model, which indicates that anyone can participate in and contribute to OWASP-related projects, online chats and more. For everything from videos and online tools to events and forums, the OWASP ensures that its offerings remain free and easily accessible via its website.
The OWASP Top 10 provides rankings of- and remediation guidance for the top ten most critical web application security risks. Leveraging the comprehensive knowledge and experience of the OWASP’s open community contributors, the report is based on a consensus among security experts globally.
Threats are ranked according to the frequency of discovered security defects, the magnitude of their potential effects, and the severity of the uncovered vulnerabilities. The report aims to provide web application security professionals and application developers insight into the most critical security risks to fold the report’s findings and recommendations into their security practices, thus reducing the presence of known risks in their applications.
How does the Open Web Application Security Project Work?
The group supporting OWASP is composed of a range of web security specialists spread over the globe. They share their experiences and knowledge of existing countermeasures, attacks, threats and vulnerabilities.
The idea is to collect the most important information that enables the assessment of security risks and how to fight them efficiently.
Why OWASP is important?
Among the key benefits that OWASP provides to IP professionals and companies, we can highlight the following:
- Boosts the image of the software developer company
- Increases the potential for application success
- Contributes to stronger encryption
- Assists in reducing the rate of errors and operational failures in systems
- Assists in making applications more armored against cyber attacks
What is the OWASP Top 10?

The OWASP Top 10 list the ten most common and critical security vulnerabilities, ranked according to the severity of the security flaw they each constitute. As mentioned earlier, the list is based on a consensus of security experts worldwide and is one of the most beneficial resources in a budding security professional’s toolkit.
How are the top 10 vulnerabilities used, and Why is OWASP Top 10 such a big deal?
The OWASP Top 10 is maybe the most ubiquitous and well-known security resource out there, and it is recognized even outside application security circles. It is often the first tool in a security engineer’s toolkit since it highlights the most common threats in software. Development and technology methods evolve rapidly, and so must our methods to mitigate security threats. The annually upgraded list ensures both security professionals and developers are aware of the vulnerabilities they are most likely to face.
Additionally, the OWASP Top 10 provides a way for security engineers to gauge the severity of a vulnerability- the higher up it is on the list, the more vital it is. This is the easiest benchmark to determine which application security vulnerabilities need to be remediated first.
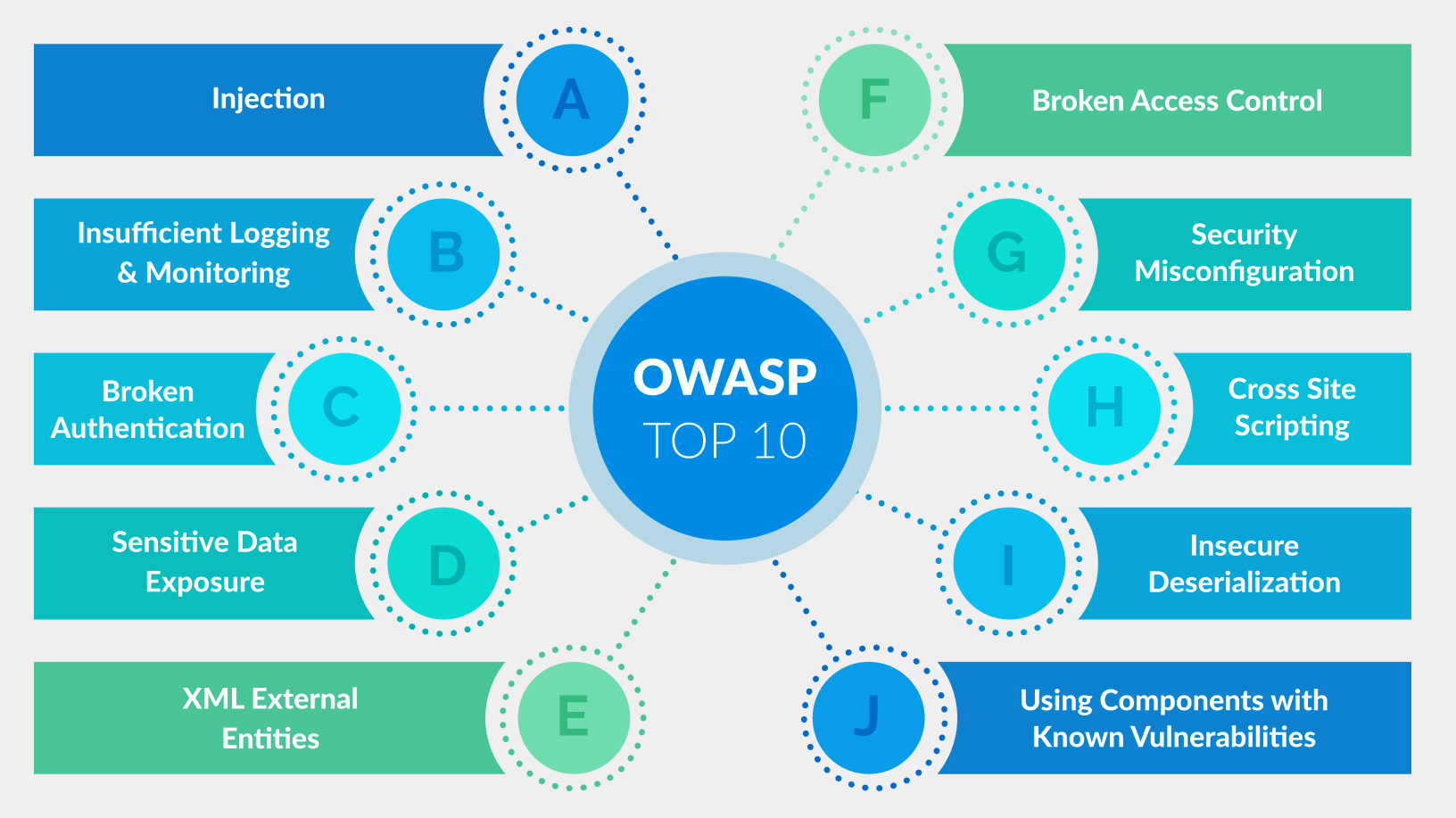
Top 10 web application security risks
One of OWASP’s flagship projects is the publication of the OWASP 10, which highlights the top ten security risks across the internet. This standard awareness document represents a broad consensus about the most common attacks on web applications.
Broken access control
Broken access control moves up from the fifth position- 94-per cent of applications were tested for some form of broken access control. Generally, 34 common weakness enumerations (CWEs) mapped to Broken Access Control had more occurrences in applications than any other category.
Injection Attacks
Injection slides down to the third position. 94-per cent of the applications were tested for any form of injection, and the 33 CWEs mapped in this section have the second most occurrences in software. Crosssite Scripting is now part of this listing in this edition. Injection attacks happen when untrusted data is interpreted and injected into a query like LDAP, NoSQL, OS, SQL or any other user input field, leading to the executing of unintended commands or unauthorised access to information.
How to prevent injection attacks
- Deploy LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection
- Deploy positive or “whitelist” server-side input validation
- Use safe APIs which prevent the use of the interpreter entirely
- Escape special characters
- Use Modern application security testing tools like Seeker to secure the application during the test stages and check for injection attacks. For instance, it can identify NoSQL injections, command injections, LDAP injections, template injections, and log injections.
Vulnerable and outdated components
Vulnerable and outdated components were previously titled deploying components with known vulnerabilities and are #2 in the Top ten community categories. It moves up from #9 in the last update. It is known that we struggle to test and evaluate risk. It is the only category not to have any (CVEs) Common Vulnerability and Exposures mapped to the included CWEs; thus, default exploits and impact weights of 5.0 are factored into their scores. Remove unused dependencies, documentation, files, components, and unnecessary features to prevent Vulnerable and Outdated Components
Security misconfiguration
Security misconfigurations shifts from #6 in the previous edition; 90-percent of applications were tested for some form of misconfiguration. With more shifts into highly configurable software, it is not surprising to see this section move up. The former listing for XML External Entities (XXE) is now part of this section.
Insufficient logging and monitoring
Without sufficient security logging and monitoring of an internal system and inefficient incident response, attackers can penetrate a system and keep on getting access to more systems and extracting, destroying or tampering with user’s data. Note that logging and monitoring failures can directly impact forensics, alerting, incident and visibility.
Using components with known vulnerabilities
Software components run with the safe level of access as the application itself; thus, if a threat in a component can be exploited, it might compromise the application’s defenses against attacks.
Insecure deserialization
Flaws in the deserialization of APIs can lead to remote code execution, injection tracks, privilege escalation, and replay attacks. One method of presenting this is to deny calibrated objects from untrusted sources.
XSS(Cross-Site Scripting)
When untrusted data in a new web page is not correctly validated or escaped, attackers can use XSS to execute scripts in a user’s browser to hijack their session, perform unintended site actions or redirects to malicious sites.
Cryptographic failures
Previously ranked in position three and formerly known as sensitive data exposure, this entry was renamed cryptographic failures to portray it accurately as a route cause instead of a symptom. Cryptographic features happen when important stored or transmitted data ( such as credit card or social security number) is compromised. The Black Duck cryptography modules surface the cryptographic methods deployed in open source software (OSS), so they can be further assessed for strength. Both Black Duck software composition analysis and Coverity Static Application Security Testing have checkers that can offer a point in time snapshot at the code and component levels.
Broken authentication
When user authentication and session management are incorrectly managed, attackers can gain access to user accounts, passwords, keys, and session tokens or exploit the system to presume the identity of other users.
Preventing identification and authentication failures
- Limit or delay failed login attempts
- Harden all authentication-related processes such as credential recovery and registration
- Deploy the guidelines in NIST 800-63 B Section 5.1.1 for Memorized Secrets
- Look for a list of the top 10 000 worst passwords
- Do not use systems with default credentials
- Adopt multi-factor authentication
Server-side request forgery (SSRF)
An SSFR attack happens when a web application makes a request for a remote resource without validating the URL supplied by the user. The hackers induce the app to make requests to their chosen domain, thus putting the application at serious risk.
A successful SSRF attack can enable the malicious actor to access data within the company and, in certain cases, even execute commands.
Steps to prevent Server-Side Request Forgery
- Disable HTTP redirections
- Do not send raw responses to clients
- Enforce the URL port, schema, and destination with a positive allow list
- Sanitize and validate all client-supplied input data
Which security vulnerabilities are new/ have been removed from the list?
The OWASP has maintained its Top 10 list for a while now, and it updates it every two or three years according to advancements and changes in the AppSec market. Here are common vulnerabilities that have been added or removed from the list.
| NEW | Entering the list At #4, Insecure Design is a new vulnerability that reflects the increasing focus on shifting justify and consolidating security into the whole software development lifecycle. It calls for more secure design patterns, threat modeling, and reference architectures. |
| NEW | Server-Side Request Forgery entered the list at number 10. Typically this was the #1 result voted by users in the OWASP community survey. |
| NEW | Software Application and Data Integrity Failures entered the list at #8, concentrating on the integrity of software updates and CI/CD pipelines. This is a response to the huge effect of supply chain attacks. |
| REMOVED | XML External Entities (XXE) and Cross-Site Scripting are removed and merged into other categories (Security Configuration and Injection, respectively). The best way to prevent an XEE attack is to have web applications accept a less complex type of data, such as JSON**. |
How to keep your web applications secure in the future

Remember that the OWASP Top ten threats are the most trivial out of the many vulnerabilities cybercriminals can manipulate and exploit. Companies may overlook web applications when they create their security strategies, or they might presume their web applications are protected by their network firewalls.
To help defend against the common web application security threats, we covered in this post, consider including a web application firewall in your company’s security strategy and technology stack to ensure you produce a more secure code. You can also learn more about how to strengthen your cybersecurity with OWASP’s documents, free tools, methodologies, guides, presentations and videos.
Security Testing: how can Synopsys help?

Most companies deploy many application security tools to assist in checking off OWASP compliance requirements. Whereas this is a good application security practice, it is not sufficient- companies still face the problem of normalizing, correlating and aggregating the different findings from the various AST tools. This is where (ASOC) application security orchestration and correlation tools improve team productivity and process efficiency.
Having an ASOC solution can help proactively track and address violations of OWASP Top 10 standards. ASOC solutions such as Synopsys Code and Intelligent Orchestration can contextualize high-impact security activities depending on compliance violations and application risk assessment.
These solutions provide a frictionless means to visualize and adopt OWASP standards early because they integrate with developer tools and frameworks that support continuous tracking, penetration testing and management of security activities and findings. For example, Code DX can centrally consume results from all AST tools (commercial, open-source, SCA, DAST, and SAST), correlate these findings, consolidate them by type, and allow users to view which findings constitute violations of OWASP standards via the built-in compliance reporting capability.
Additional application testing can then be managed via Intelligent Orchestration, which can determine the kind of testing needed and the business criticality of the software to be tested. Whilst AST tools provide sensitive information to address individual OWASP standards, an ASOC approach can assist, facilitate and orchestrate repeatable software application quality control and operations across all AST problems.