Introduction
We are fervent supporters of protecting your source code and the secrets contained within it throughout its lifecycle and at all points of your supply chain, whether we’re explaining why You Should Care About Securing Your Source-Code or warning you about The Bad Coding Habits That Leave Your Source Code Exposed. Adhering to a dependable compliance model is one of the first and best methodologies that can help you get there.
In this article:
- Who is OWASP?
- What is the OWASP SAMM Framework?
- A Simple Framework
- The OWASP SAMM Framework, in Layman Terms
- Security Knowledge Framework
- OWASP Application Security Verification Standard
- What really is ASVS?
- SKF Features
- Testing Techniques Explained
- OWASP Web Security Testing Guide
- FAQs
Who is OWASP?

OWASP (Open Web Application Security Project) is a non-profit organization dedicated to software security. OWASP has thousands of members spread across the world in hundreds of chapters that support open source projects and hold educational conferences.
The OWASP Foundation, established in 2001 and is funded by corporations, foundations, developers, and volunteers. The Foundation has become an authoritative voice in cyber security, thanks to the support of so many tech industry players and its global reach. For example, OWASP publishes their Top Ten document on a regular basis, which raises web application security awareness by highlighting the top ten web application security risks. MITRE, PCI DSS, the Defense Information Systems Agency, and the United States Federal Trade Commission are just a few of the major organizations, books, and other publications that reference the OWASP Top Ten that represents a broad consensus about what the most critical Web application security flaws are.
OWASP creates a plethora of projects and reference material, but today we want to focus on their SAMM project in particular.
What is the OWASP SAMM Framework?
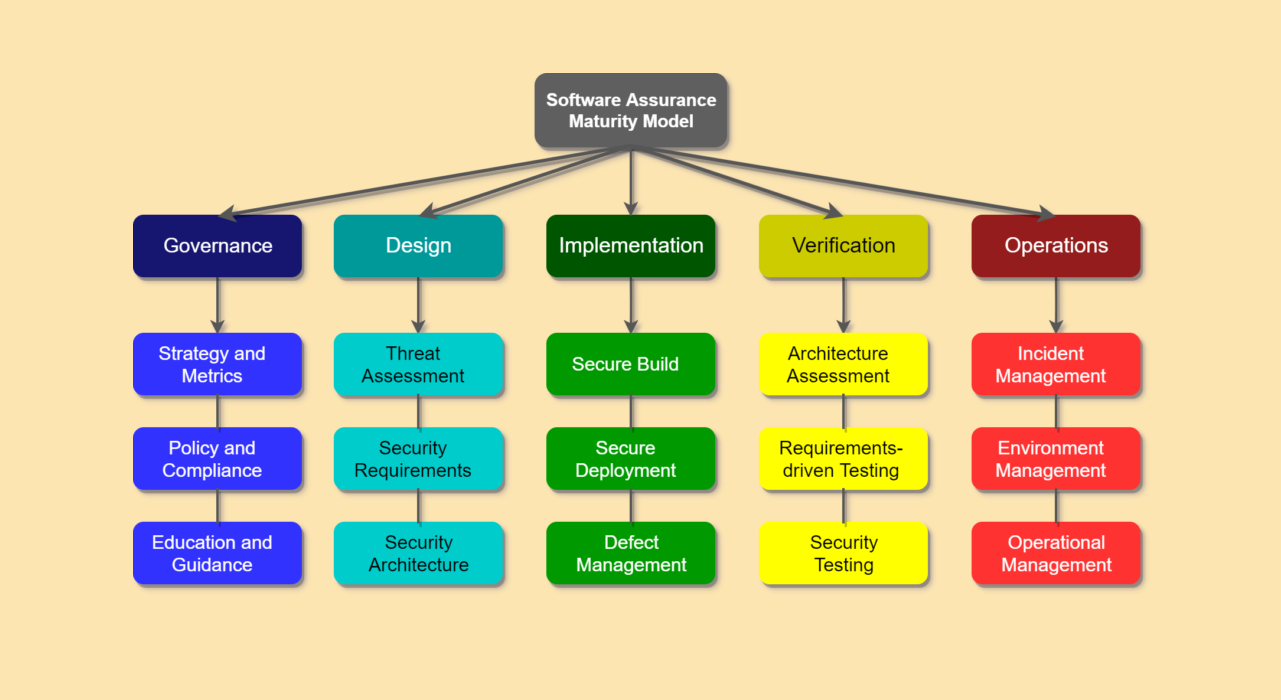
SAMM stands for Software Assurance Maturity Paradigm, a software security compliance model established by OWASP and supported by a number of industry groups. Following industry best practices, particularly when framed through a solid and authoritative model, is always a more reliable way to steer your ship than making it up as you go. SAMM is worth the expense of adoption because of the experience, history, and industry support that OWASP brings to the table. You can be confident that you are better prepared for risks to your source code if you implement and closely adhere to such a model within your organization.
A Simple Framework
While security is critical, installing a new framework throughout your whole software supply chain is a major undertaking. What we appreciate about SAMM is that it’s both easy to use and flexible, even if you don’t have any technical knowledge. SAMM may be tailored to match your needs and implemented in the least disruptive manner possible, whether you’re a tiny software startup or a huge business with various teams and roles involved in the development process.
The OWASP SAMM Framework is based on twelve fundamental security principles that are separated into three maturity levels and organized into five business functions. Each business function has two streams (groups of activities).
The model’s maturity levels are where it adapts to your own company circumstance. Your organization’s maturity level is determined by the security measures you already have in place. Then it’s up to you to decide what maturity level you want to reach, which will differ from one business to the next. SAMM is fortunate in that it is not a one-size-fits-all solution, and its flexibility is its primary selling point.
SAMM is implemented in six steps, the first four of which can be completed in a few days by a single person. It’s Free!
Every security solution vendor (including us) wants a piece of your wallet (call us prejudiced, but we think Cycode is worth it). The OWASP SAMM Framework, on the other hand, is completely free to use and, like all open-source projects, is community-supported.
Simply follow the fast start instructions to get started, then examine your organization’s status and requirements. You can even use OWASP’s assessment toolbox as a reference. You may get a free guide to help you adopt SAMM in an Agile manner, and you can also get free support from their Slack and Google Groups forums. OWASP mission is to make application security “visible,” so that people and organizations can make informed decision about app security risks.
The OWASP SAMM Framework, in Layman Terms

We’ve thrown a lot of perks and connections at you in our excitement, but perhaps you’re thinking to yourself, “Ok, sounds wonderful — but I need a basic description of what this is.” It’s no problem! First and foremost, the approach is built around twelve security practices. A “practice” is a collection of security-related tasks.
These twelve activities are divided into five business functions by SAMM. Various departments/functions/teams are most likely involved at various stages of the software development lifecycle. Various five business functions are dispersed throughout these organizations. Everyone who works with your program bears some level of obligation.Now, let’s get back to the practices: A single practice’s activities are separated into two “streams.” Each stream has a goal that can be achieved at various stages of maturity.
Finally, activities are categorized into three levels of maturity. Lower maturity activities are simpler and less formal, whereas higher maturity activities are more complex and formal.
So here’s what it looks like:
The OWASP Security Knowledge Framework is a free, open-source website that discusses secure coding principles in a variety of programming languages. The purpose of the OWASP-SKF is to assist you in learning about and incorporating security by design into your software development, as well as building secure by design applications. OWASP-SKF does this through easily manageable software development projects that include checklists (using OWASP-ASVS/OWASP-MASVS or bespoke security checklists) and security validation laboratories (using SKF-Labs, OWASP Juice-shop, and best practice code examples from SKF and the OWASP-Cheatsheets).
Security Knowledge Framework

The OWASP Security Knowledge Framework (SKF) is a Python-Flask web application that use the OWASP Application Security Verification Standard to teach developers how to write secure code by design. The OWASP Security Knowledge Framework is extremely relevant to contemporary application security and should be necessary in any enterprise for developer training, security research, and security requirement collecting.
SKF assists and empowers developers by providing them with the necessary information and awareness to design secure apps. Everything is ready for Kubernetes platforms, as well as docker-compose and bare-metal/on-premise deployments.
SKF has:
- Knowledge Base items to assist you in learning more.
- Checklist – SKF includes ASVS and MASVS right out of the box.
- Suggestions for implementing security needs
- To test actual vulnerabilities, labs are used.
- And there’s more.
SKF is also adaptable! Create or alter your own checklist. It can be altered and adapted as needed as a framework. The SKF team is attempting to assist developers in understanding how to secure their applications and empowering them to perform some of the verification work themselves. You can also start conducting the labs by going to the SKF URL.
Developers can shine with the SKF, creating cool apps that are secure by design in a very systematic manner.
The OWASP Risk Assessment Framework
Although there are many SAST tools available for testers, the compatibility and environment setup process is complex. Testers will be able to interpret and review their code quality and vulnerabilities using the OWASP Risk Assessment Framework’s Static Application Security Testing tool without any additional setup. To assist developers in writing and producing secure code, the OWASP Risk Assessment Framework can be integrated into the DevSecOps toolchain.
OWASP Application Security Verification Standard
What really is ASVS?
The OWASP Application Security Verification Standard (ASVS) Project is a way of testing web application technical security controls. It also gives developers a list of things they need for secure development of apps.
The OWASP Application Security Verification Standard (ASVS) Project’s main goal is to standardize the breadth of coverage and rigor accessible in the market when it comes to performing Web application security verification with a commercially viable open standard. The standard establishes a framework for evaluating application technical security measures, as well as any other technical security-controls in the environment, that are used to protect against vulnerabilities like Cross-Site Scripting (XSS) and SQL injection. This standard can be used to achieve a level of trust in Web application security. The specifications were created with the following goals in mind:
|
Provide a yardstick for application developers and owners to use in determining the level of trust that may be placed in their Web apps. |
|
Provide security control developers with recommendations on what to include in security controls to meet application security needs, and |
|
Provide a foundation for contracting application security verification criteria. |
How To Reference ASVS Requirements
Each condition has an identifier in the format “chapter”. “section”.<requirement> where each element is a number.
- The <chapter> value corresponds to the chapter in which the requirement is found.
- The “section” value correlates to the section within that chapter where the requirement appears.
- The <requirement> value determines the specific requirement within the chapter and section.
Check for thread safety and resistance to time-of-check and time-of-use race conditions in all high-value business logic flows, such as broken authentication, session management, and broken access control.
Because the identifiers of the standard may change between versions, it is preferable that other documents, reports, or tools use the format: <version>-chapter>.section>.requirement>, where’version’ is the ASVS version tag. v4.0.3-1.11.3, for example, would be understood to mean the third requirement in the ‘Business Logic Architecture’ section of the ‘Architecture’ chapter from version 4.0.3. (This can be shortened to vversion>-requirement identifier>.)
It is important to note that the v preceding the version portion should be lower case.
If an identification is used without the vversion> element, it is presumed that it refers to the most recent Application Security Verification Standard content. This becomes troublesome when the standard evolves and changes, which is why writers and developers should add the version element. ASVS requirement lists are accessible in CSV, JSON, and other forms, which can be used for programmatic or reference purposes.
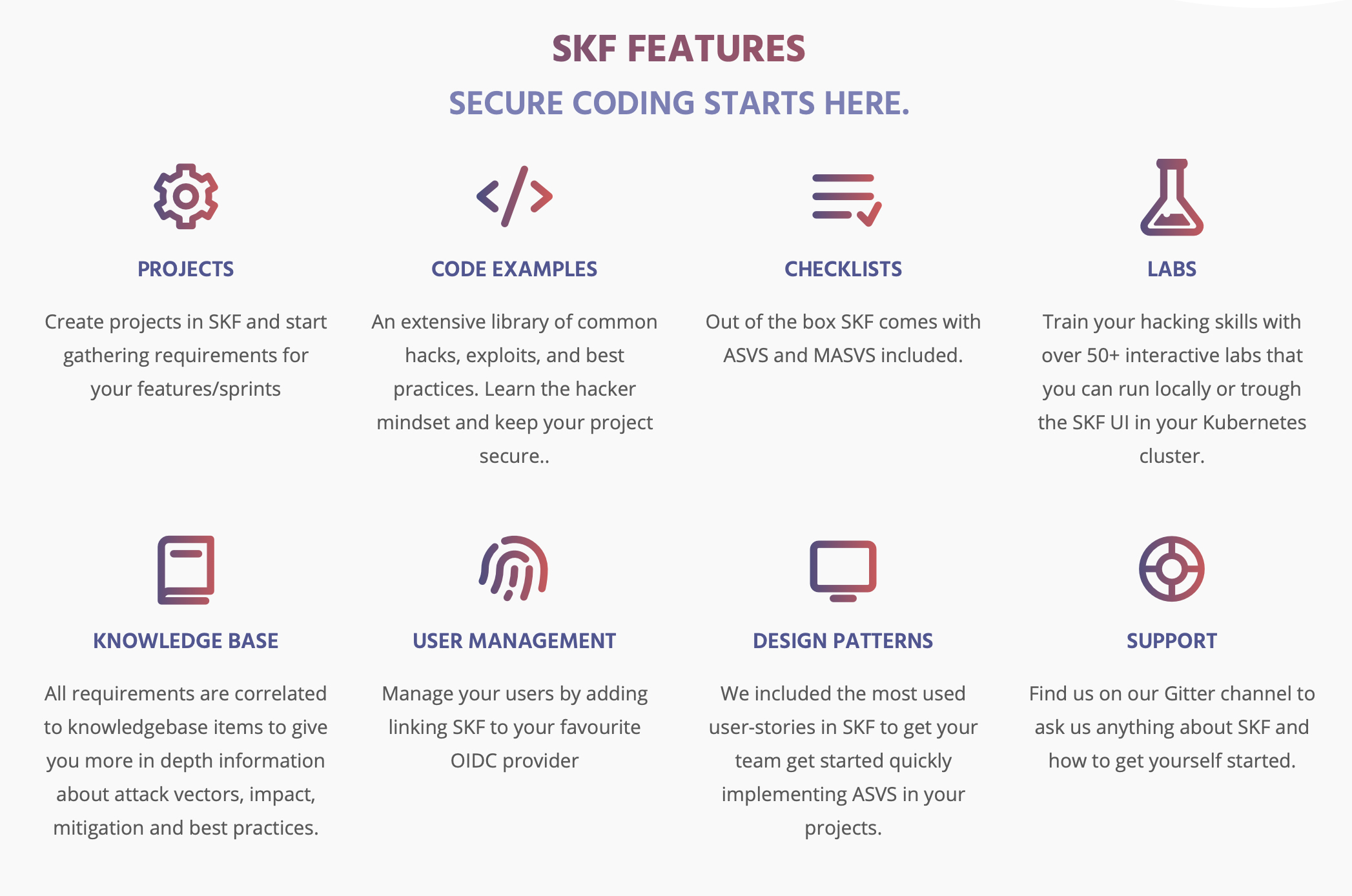
SKF Features
Projects
Begin by creating projects in SKF and gathering requirements for your features/sprints.
Code Examples
A large collection of common hacks, exploits, and best practices. Learn how to think like a hacker and keep your project safe.
Checklists
ASVS and MASVS are included in the box with SKF.
Training platform
Over 150+ interactive labs that you can run locally or through the SKF UI in your Kubernetes cluster to hone your secure coding and hacking skills.
Knowledge Base
Over 150+ interactive labs that you can run locally or through the SKF UI in your Kubernetes cluster to improve your secure coding and hacking skills.
User Management
Link SKF to your favorite OIDC supplier to manage your users.
Design Patterns
In SKF, we’ve included the most often utilized user-stories to help your team get up and running quickly with ASVS in your projects.
Testing Techniques Explained
This section gives a high level overview of the many testing methodologies that can be used to create a testing program. It does not give precise methodology for these strategies. This section is included to set the stage for the framework presented in the following chapter and to illustrate the benefits and drawbacks of some of the strategies to consider. We’ll go through the following topics in particular:
- Manual Inspections and Reviews
- Threat Modeling
- Code Review
- Penetration Testing
Manual Inspections and Reviews
Human assessments of people, rules, and procedures are called manual inspections. Inspections of technology decisions, such as architectural designs, can also be done manually. They are normally carried out by reviewing documentation or conducting interviews with the designers or owners of the system.
Manual inspections and human reviews, while simple in idea, can be among the most powerful and successful methods available. The tester can rapidly establish if any security risks are likely to be visible by appealing to someone how something functions and why it was built in a given way.
Advantages
- There is no support technology required.
- It can be employed in a variety of situations.
- Flexible
- Encourages collaboration
- During the SDLC’s early stages
Disadvantages
- It may be time-consuming.
- Supporting materials are not always readily available.
- To be effective, it necessitates significant human thought and skill.
Threat Modeling
Threat modeling is a popular technique for assisting system designers in considering the security threats that their systems and applications may face. As a result, threat modeling can be viewed as an application risk assessment. It allows the designer to develop mitigation strategies for potential vulnerabilities and assists them in focusing their inevitably limited capabilities and attention on the parts of the system that require it the most. It is recommended that a threat model be developed and documented for all applications.
Advantages
- Early in the SDLC,
- the attacker’s practical view of the system is flexible.
Disadvantages
- Good threat models do not always imply good software.
Source Code Review
Good threat models do not exist. The process of manually checking the source-code of a web application for security flaws is known as source code review. Many serious security flaws cannot be detected using any other method of analysis or testing. Almost all security professionals agree that there is no substitute for actually inspecting the code. All of the information needed to identify security flaws is somewhere in the code. In contrast to testing closed software such as operating systems, when testing web applications (especially if developed in house), the source-code should be made available for testing.
Advantages
- Effectiveness and Completeness
- Accuracy
- Fast (for competent reviewers)
Disadvantages
- High-skilled security-aware developers are required.
- Issues in compiled libraries may go unnoticed.
- It is difficult to detect runtime misconfiguration.
- The source code that is actually deployed may differ from the one that is being analyzed.
Penetration Testing
For decades, penetration testing has been a common technique used to test network security. It’s also referred to as black-box testing or ethical hacking (Such as Glenn ten Cate
). Penetration testing is the “art” of remotely testing a system or application to find security vulnerabilities without noticing the inner workings of the target. In most cases, the penetration test team can access an application as if they were users. The tester takes on the part of an attacker, attempting to find and utilize vulnerabilities. In many instances, the tester will be given one or more valid system accounts.
While penetration testing has been shown to be effective in network security, it does not naturally translate to applications. When performing penetration testing on networks and operating systems, the majority of the work involves locating and exploiting known vulnerabilities in specific technologies. Penetration testing in the web application field is more similar to pure research due to the fact that web applications are almost entirely bespoke. Although some automated penetration testing tools have been developed, their effectiveness alone can be limited due to the bespoke nature of web applications.
Advantages
- Can be quick (and therefore cheap)
- It necessitates fewer skills than source code review.
- The code that is actually exposed is tested.
Disadvantages
- Front-impact testing is too late in the SDLC.
OWASP Web Security Testing Guide

The Web Security Testing Guide (WSTG) Project creates the industry’s most comprehensive cybersecurity testing resource for web application developers and security professionals. The WSTG is a thorough guide for testing the security of web applications and web services. The WSTG, which was created through the collaborative efforts of cybersecurity professionals and dedicated volunteers, provides a framework of best practices used by penetration testers and organizations worldwide.
FAQs
What is application security?
Application security, or appsec, is the practice of protecting computer applications from external security threats by utilizing security software, hardware, techniques, best practices, and procedures.
Once upon a time, security was an afterthought in software development. It is now an increasingly important concern for all aspects of application development, from planning to deployment and beyond. The number of applications developed, distributed, used, and patched across networks is rapidly increasing. As a result, application security practices must address a wider range of threats.
What does server side mean?
‘Server side,’ like ‘client side,’ refers to everything that occurs on the server rather than the client. Previously, nearly all business logic was executed on the server side, including dynamic webpage rendering, database interaction, identity authentication, and push notifications.
The issue with hosting all of these processes on the server side is that each request involving one of them must travel from the client to the server every time. This adds a significant amount of latency. As a result, modern applications run more code on the client side.
What is XML?
XML is a tool for storing and transporting data that is independent of software and hardware.
What is API?
API(Application Programming Interface), and it is a software intermediary that allows two applications to communicate with one another. An API is used every time you use an app like Facebook, send an instant message, or check the weather on your phone.
What is Cross-Site Request Forgery (CSRF)?
Cross-Site Request Forgery (CSRF) is an attack that forces an authenticated end user to perform unwanted actions on a web application. An attacker can trick users of a web application into performing actions of the attacker’s choosing with the help of social engineering (such as sending a link via email or chat). If the casualty is a normal user, a successful CSRF attack can force the user to perform state-changing requests to external entities such as transferring funds, changing their email address, and so on. CSRF can compromise the entire web application if the victim is an administrative account.