Web Application Security: Definition & Best Practices
Application security is a crucial part of the software development life cycle, and getting it right should be a top priority in today’s ever-advancing digital ecosystem. The rise of new architectures such as frameworks and cloud-native offers new attack surfaces. Application security outlines security measures at the application level to prevent code or data within the application from being hijacked or stolen. It comprises security considerations that happen during software application development and design. It also entails approaches and systems to protect apps after they get used.
Today businesses invest a lot of time and money in processes and tools that help secure their applications throughout the software development lifecycle. Achieving application security has become challenging for DevOps, software engineers, and security professionals as application systems become more complex, and hackers constantly increase their efforts to target the application layer. This article will take a deep dive into application security and discuss how software development organizations can ensure they have all the tools to address application security threats effectively.
Table of contents:
- What is application security, and why is it important?
- Why application security is important
- Types of application security
- What is Static application security testing (SAST)?
- Benefits of static application security testing to developers
- What are application security risks?
- Application security vs. network security
- How does a web application firewall help with application security?
- Application security at the speed of DevSecOps
- Application Delivery in VMware
What is Application Security and Why is it Important?

What do you mean by Application Security in Cybersecurity
Application security is the process of testing, adding, developing, and testing security features within applications to prevent security vulnerabilities against risks such as data breaches, modification and unauthorized access.
It is the discipline of practices, tools, and processes that aim to protect applications from threats throughout the application lifecycle. Generally, cybercriminals are motivated, specialized, and organized to find and exploit vulnerabilities in organization applications to steal data, sensitive information, and intellectual property. Application security can help businesses protect all types of applications (such as microservices, mobile, web, desktop, and legacy) used by employees and external stakeholders, including employees, business partners, and employees.
Application software security is one of the various levels of security that companies use to protect systems. Other levels of security include endpoint, network security, operating system, or mobile security. Application security is also vital for mobile applications stores, where hackers try to attach various types of malware to less vetted mobile apps.
Why Application Security is Important
Today’s software applications are often available over various networks and connected to the cloud; they are more vulnerable to security breaches and attacks. There is increasing incentive and pressure to ascertain security at the network level and within individual applications. One cause of this is that hackers are concentrating on attacking applications more now than before. Application security testing can uncover application-level flaws, assisting in preventing these attacks.
The earlier and faster you can detect and resolve security issues in the software development process, the safer your business will be. Since everyone makes mistakes, the trick is to recognize them as soon as possible.
Software application security tools that integrate with your development environment can make this workflow and process much simpler and more efficient. These tools are specifically beneficial for compliance audits since they can save time and resources by detecting issues before the auditors notice them. The transforming nature of how enterprise applications are designed over the last years has aided the rapid expansion of the application security industry.
Types of Application Security

Different types of application security functionalities include logging, encryption, authorization, authentication, and application security testing. Software developers can also code applications to lower security vulnerabilities.
- Application security testing: A vital process to ensure that these security controls work correctly.
- Logging: Logging can assist in identifying who got access to the data and how if there is a security breach in an application. Application log files offer a time-stamped record of which aspects of the software application were accessed and by who.
- Encryption: Once an individual has been authenticated and utilizes the application, other security policies can protect sensitive information from being used or seen by a cybercriminal. In cloud-based applications, where traffic comprising of sensitive data travels between the cloud and the end-user, traffic can be encrypted to keep the information/data safe.
- Identification: It is vital to ensure that all breaches and their sources have been identified correctly. This can be achieved by confirming that attack validation checks are correlated to ensure there are no false positives.
- Authorization: Following the authentication of a user, the user might be authorized to access and use the software application. The system can confirm that a user has been authorized to access the web application by comparing the user’s identification with a list of authorized end users. Authentication should happen before authorization so that the software matches only validated user credentials to the authorized user list.
- Authentication: This happens when developers build procedures into an application to ensure that only authorized users access it. Authentication processes ensure that a user is who they say they are. This can be attained by requiring the user to provide a password and a username when logging in to an application. Generally, multi-factor authentication requires more than one type of authentication- the factors might include something you know (password), something you are (facial recognition or thumbprint), and something you have (a mobile device).
Application Security Tools

Many application security software product categories revolve around application shielding products and security testing tools. The latter is a more mature market with many well-known vendors; some of them are the lions of the software industry, such as MicroFocus, CA, and IBM. These application security tools are well enough that Gartner has developed its Magic Quadrant and classified their success and importance. Additionally, review sites like IT Central Station have been able to survey and rank these vendors, too.
Gartner classifies the security testing tools into various broad buckets, and they are somehow beneficial for how to decide what you need to protect your app portfolio:
- Mobile testing: This type of application security tool is designed specifically for mobile environments and can assess how an attacker can leverage the mobile OS and the applications running on them in its entirety.
- Interactive testing: It mixes elements of both dynamic testing and static testing.
- Static testing: This technique analyzes code at fixed points during the development. This is beneficial for software developers to check their code as they write it to ensure that security problems are being introduced during development.
- Dynamic testing: Dynamic testing analyzes running code. This is more beneficial since it can stimulate attacks on production systems and reveal more sophisticated attack patterns that deploy a combination of systems.
Another way to look at the application security testing tools is how they are delivered, either through a SaaS-based subscription service where you submit your code for online analysis or through an on-premises tool.
One issue is the programming language supported by each testing vendor. Some vendors limit their tools to just one or two programming languages (JAva is often a safe bet). Others are more involved with the Microsoft .Net universe. The same applies to integrated development environments: some tools work as extensions or plug-ins of these IDEs, so testing your application code is as simple as clicking on a button.
Another caveat is if any tool is isolated from other testing results or included in its analysis. IBM is one of the few that can import findings from penetration testing, manual code reviews, competitor’s tests, and application vulnerability assessments. This can be beneficial, particularly if you have many tools for securing tools applications that you need to keep track of.
Let us not forget about app shielding tools. The primary purpose of these tools is to harden the application so that attacks are more challenging to carry out. This is a less charted territory. Here you will find a vast collection of small, point products that in many cases have limited customer bases and history. These products aim to do more than just test for vulnerabilities and actively prevent your applications from compromise or corruption. They comprise a few different broad categories:
- Threat detection tools: These tools assess the network or environment where your apps are running and make assessments about possible threats and misused trust relationships. Some tools provide device fingerprints to determine if a mobile phone has been rooted or compromised.
- RASP (Runtime application self-protection: These tools could be regarded as a combination of shielding and testing. They offer a measure of protection against possible reverse-engineering attacks. Generally, RASP tools constantly monitor the application’s behavior, which is beneficial particularly in mobile environments when apps can be written, have privilege abuse to turn them into doing nefarious things or run on a rooted phone. RASP tools can terminate the errant processes or send alerts if the application is compromised. RASP will probably become the default on many mobile development environments and built-in as part of other mobile app protection tools.
- Anti-tampering and encryption tools: These are other application security programs that can be used to keep hackers from gaining access to your code.
- (IAST) Interactive application security testing: Integration of dynamic testing and runtime analysis to identify more security vulnerabilities by exposing exploits better than dynamic testing alone and expanding coverage of the attack surface.
- Code obfuscation: Hackers usually use obfuscation methods to hide their malware, and now tools enable developers to help protect their application code from being attacked.

What is Static Application Security Testing?
Static application security testing SAST (Static application security testing) scans the application source files to help remediate the underlying security flaws.
Benefits of static application security testing to developers
- Fully integrated with an integrated developer (IDE)
- Review static analysis scan leads to real-time access to recommendations, line-of-code navigation to find web application vulnerabilities easier, and collaborative auditing
- Identify and get rid of vulnerabilities in source, byte code, or binary.
What is Dynamic Application Security Testing?
(DAST) Dynamic Application Security Testing simulates controlled attacks on a running web service or application to identify exploitable vulnerabilities in a running environment.
What are the benefits of dynamic security testing:
- Tests functional app, contrary to SAST, is not runtime, language constrained, and environment-related issues can be discovered.
- The dynamic analysis allows a broader approach to managing portfolio risk and scanning apps as part of risk management.
- It can be integrated into QA, Dev, and Production to provide a continuous holistic view.
- Offers an extensive view of application security by concentrating on what is exploitable and covering all elements (services, open source, custom size, and server)
Application Security Approaches
Various approaches will uncover different subsets of the application’s security flaws, and they will be most effective at different stages of the software development lifecycle. They reflect the various vulnerability, costs, effort, and time trade-offs.
| Application security approach | Description |
| Coordinated vulnerability platform | The majority of websites and software providers provide hacker-powered application security solutions through which individuals can be compensated and recognized for reporting defects. |
| Automation/automated tooling | Most security tools can be automated by including them in the testing or development process. Automated SAST/SAST tools incorporated into CI/CD systems, Code editors or software composition analysis are examples. |
| Black-box security audit | This is achieved solely via an application to test it for security flaws, and source code is necessary. |
| Code review or white-box security review | A security engineer delves into the software by manually inspecting the source code and looking for security flaws. Flaws unique to the application can be discovered via understanding the application. |
| Design review | The design and architecture of the application can be assessed for security issues before code is created. The development of a threat model is a famous strategy used at this phase. |
What are Application Security Risks?

Security challenges with web applications range from focused database tampering to large-scale network disruption. Each risk is rated based on the frequency that it is the root cause of a vulnerability and the severity of its exploitation. Here are some of the security threats:
- The buffer overflow happens when malicious code is injected into the system’s designated memory region. Typically overflowing the buffer zone’s capacity makes the surrounding areas of the application’s memory overwritten with data, thus posing a security threat.
- Memory corruption happens when bad actors execute various attacks on the application, they end up unintentionally changing some area of its memory. As a result, the software application exhibits unexpected behavior or fails.
- Hackers use cross-site request forgery (CSRF) to mimic authorized users after dumping them into submitting an authorization request. Because their accounts have extra permissions, high-level users are obviously frequent targets of this approach, and after the account is compromised, the attacker can change, destroy or remove data.
- (SQLi) SQL injection is a strategy used by hackers to exploit database vulnerabilities. These attacks can reveal user passwords and identities, allow attackers to destroy or edit data, and create or create user rights.
- Remote attackers can employ distributed denial-of-service (DDoS attacks) or denial of service (DoS) attacks to flood a targeted server or/and the infrastructure that supports it with various types of traffic. Eventually, this legitimate traffic prevents legitimate users from accessing the server, leading to shut down.
- A vulnerability known as cross-site scripting XSS enables an attacker to insert client-side code into a webpage. This provides the attacker with direct access to the user’s sensitive information.
Application Security vs. Network Security

A common web application security myth is that a network firewall can protect web applications and their websites. Nonetheless, network and app security are not the same. Network security deploys perimeter defenses like firewalls to keep out bad actors and grant access to safe users. For instance, administrators can configure firewalls to permit only certain users or IP addresses to access certain services.
However, these perimeter network defenses are insufficient to guard web applications against malicious attacks. This is because everyone must access business sites and web applications. Traffic coming from and to web applications thus cannot be analyzed by network firewalls, so they can not block malicious requests. If hackers want to exploit a vulnerability like SQL injection or cross-site scraping, network security will not help.
Web application security tools such as network security scanners can assist you in identifying certain problems that network security systems miss- specific web application problems such as SQL injection problems. Application security testing tools can scan all application components to ensure they are fully patched. For instance, such a tool might alert an administrator if an FTP server enables anonymous users to write to it.

Application Security in the Cloud
Application security in the cloud poses some different problems. Since cloud developers environments provide shared resources, special care should be taken to ensure that users only have access to the information they are authorized to view in their cloud-based applications. Additionally, sensitive data is also more vulnerable in cloud-based applications since that data is transmitted through the internet from the user to the app and back.

How does a Web Application Firewall help with Application Security?
Intelligent web application firewalls WAF offer an application security solution in three vital steps: mitigate, inform and inspect.
- Inspect: The system analyzes security configurations and user-to-application configurations constantly. This enables it to identify vulnerabilities and detect attacks and anomalies before too late.
- Mitigate: The WAF system enables you to work against security issues, from simple to severe, proactively. Adopt anything vital, from simple penalties to limits on blocks or traffic to specific users.
- Inform: Avi’s WAF informs your crucial staff about the security status of your apps in real-time with alerts, logs, and simple metrics that reflect risks.
Application Security at the Speed of DevSecOps
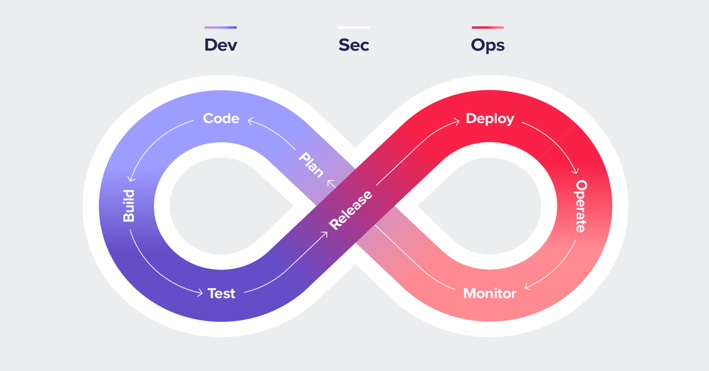
As software development cycles get shorter, developers and security professionals struggle to address security problems while keeping up with the rapidly increasing pace of application release cycles. This constant pull and push between application security needs and development speed usually result in friction between developers who do not want security to slow them down and security professionals who feel developers are neglecting security. Generally, the DevSecOps approach attempts to address this conflict and break the silos between security and developers.
DevSecOps addresses the problem of continuously increasing development and delivery pace without compromising security. First, there was DevOps, which assisted companies in creating shorter release cycles to meet the market demand of delivering innovative application software products at a rapid pace. DevSecOps adds security to the mix and integrates security through software development (SDLC) to ensure that security does not slow down development and that the development processes are secure and secure.
DevSecOps seamlessly integrates application security in the earliest stages of the SDLC by updating organizations’ application security tools and practices. It calls for modifying security testing justify to assist security teams in addressing security flaws early in development when remediation can be comparatively easy.
Application Delivery in VMware Based Data Center
Application delivery is essential because everybody uses applications- from international enterprises to small businesses to CEOs to pizza deliverers. Software applications are everywhere. An ever-expanding variety of applications and online services keep the business running. And when the applications don’t work well, neither does the company. Sadly, if the performance of a key application degrades, usually the end-user notices before the IT does; this can translate to loss of funding, loss of users, and loss of revenue. Generally, IT no longer focuses on desktops alone when managing user activities- mainly when users work with mobile devices like tablets, laptops, smartphones, etc.; the applications on the device are usually even more central to the business than desktops. Generally, IT administrators increasingly consider software applications to deliver a top priority. Many delivery application options have been developed in response to this growing need, and new terms to talk about those options.
Software application delivery, also known as app delivery, refers to any method used by IT administrators to make applications available to their end-users. App delivery includes methods like streaming, where the application is not placed on the endpoint device.
Application Security Resources

- Getting Started with Application Security in One Day-Video
- Shift justify: 3 Steps to Get Your Developers Involved in Security-Webinar
- Application Security Risk Report-Whitepaper
- Fitting Security Into Your Software Lifecycle: Automation and Integration-Webinar
- The State of Application Security in the Enterprise-Whitepaper
- OWASP Top 10 Most Critical Web Application Security Risks
- AppSec Cheat Sheet-Infographic
- The 2019 TechBeacon Buyer’s Guide to Application Security-Whitepaper